Example ADFS Configuration
Note: This Page is no longer up to date. For more updated information please see below:
Setup Guides:
- To configure Atlassian JIRA and ADFS via SAML Single Sign On (SSO) use:
Setup SAML SSO with ADFS (Jira) - To configure Atlassian Confluence and ADFS via SAML Single Sign On (SSO) use:
Setup SAML SSO with ADFS (Confluence)
It’s also possible to connect Atlassian JIRA and Confluence with Azure AD, GSuite, Okta, or virtually any other Identity Provider. Check the setup guides below, and start your 90 days free trial.
- View Setup Guides for JIRA SAML SSO and try it out here.
- View Setup Guides for Confluence SAML SSO and try it out here.
This article describes the ADFS configuration necessary for SAML Single Sign On to work.
Prerequisites
- ADFS 2.0 / 3.0
- Jira/Confluence must be accessible via HTTPS. See https://confluence.atlassian.com/display/DOC/Running+Confluence+Over+SSL+or+HTTPS for instructions.
This is necessary because ADFS accepts only HTTPS-URLs for SAML endpoints.
Configure ADFS for JIRA/Confluence single sign on
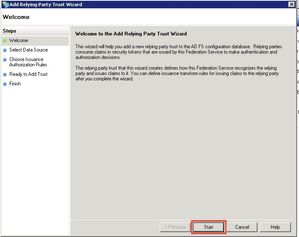
Open the AD FS 2.0 Management Console and select Add Relying Party Trust to start the Add Relying Party Trust Wizard and click Start.
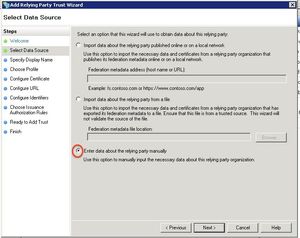
Select Enter date about the relying party manually and click Next.
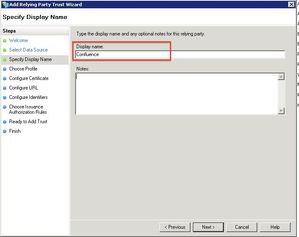
Specify a display name of your choice and click Next.
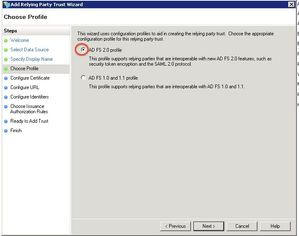
Select AD FS 2.0 profile and click Next.
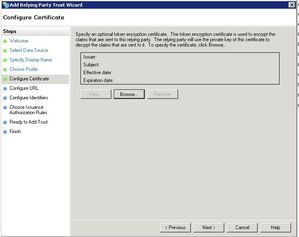
Just click Next on the Configure Certificate Page.
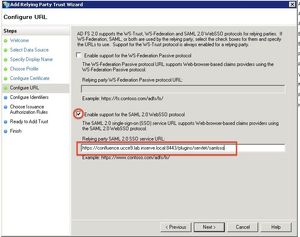
Select Enable support for the SAML 2.0 WebSSO protocol and configure the URL to the SAML plugin URL as Relying party SAML 2.0 SSO service URL.
This URL has the format https://<baseUrl>/plugins/servlet/samlsso
So if your Confluence (or Jira) is running at https://confluence.yourcompany.com/ the URL is https://confluence.yourcompany.com/plugins/servlet/samlsso
Click Next
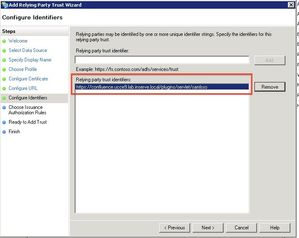
Enter the same URL as Relying party trust identifier and click Add to add it to the list. Click Next.
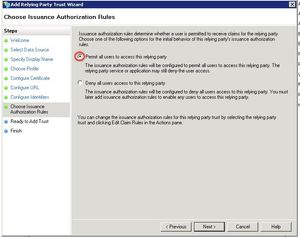
Select Permit all users to access the relying party and click Next.
This configuration defines that ADFS returns any authenticated user to Confluence or Jira. If this user's userid is not found there, JIRA or Confluence will deny access.
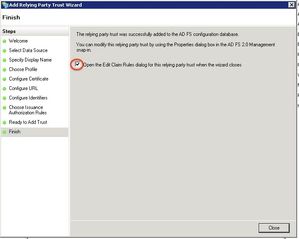
Just click Next on the next page, tick Open the Edit Claim Rules dialog and click Close.
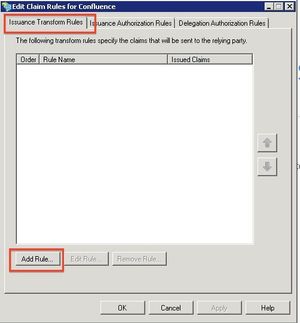
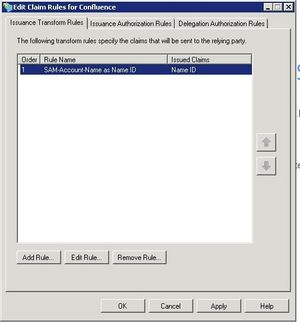
The Edit Claim Rules Window opens. I the first tab, click Add Rule
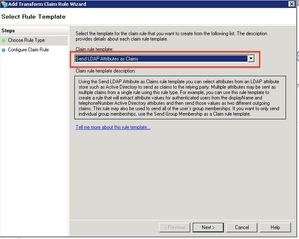
Select Send LDAP Attributes as Claims and click Next.
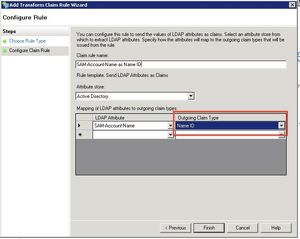
Enter a name of your choice for the rule. Select Active Directory as Attribute store. Select the LDAP Attribute containing the Confluence/JIRA userid and Name ID as Outgoing Claim Type. Click Finish.
Click OK to save the settings.
Export the ADFS token signing certificate
The SAML response coming from ADFS is signed to insure that the authentication is coming from the correct Identity Provider. To validate this signature, the certificate has to be exported from ADFS and configured in the plugin configuration.
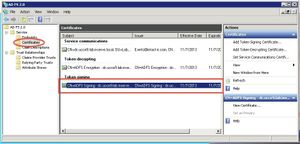
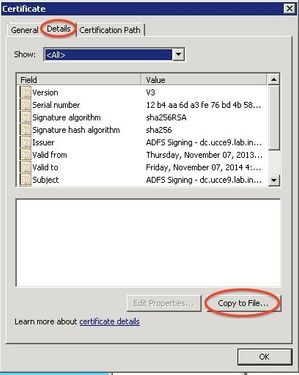
In the ADFS management console, click the Certificates folder and double-click on the Token Signing certificate.
Click the Details tab and the Button Copy To File.
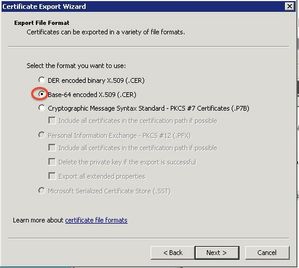
Export the certificate as Base-64 encoded X.509 (.CER).
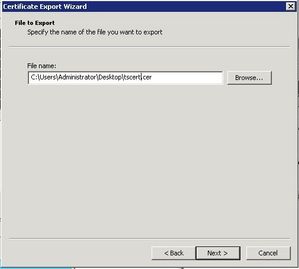
Open the exported file in a text editor and copy the content into the clipboard for the next step.
Configure the plugin
Open the SAMLSSO plugin configuration at https://<confluence/jira-url>/plugins/servlet/samlsso/admin or by clicking Configure in the Plugin Manager.
Enter the appropriate settings and click Send.
| Setting | Description | Example |
|---|---|---|
| IdP URL | URL on ADFS where the SAML authentication requests are sent to, usually https://<your-ADFS-server>/adfs/ls | https://adfs.example.com/adfs/ls/ |
| Default redirect URL | Relative URL on JIRA or Confluence to redirect to after successful login if no specific URL was called. This is usually the case if the samlsso-Servlet is opened directly. This value is usually just | / |
| Login page URL | If the SAML login fails, a link to the username/password login page is displayed in the error page. For Confluence, this is usually /login.action, for JIRA /login.jsp | /login.jsp |
| Redirect login requests | If this box is checked, JIRA/Confluence redirects to the samlsso-Servlet (which redirects to ADFS) instead of the login page. If this is box is not checked, single sign on only works if the samlsso-Servlet is called directly at https://<confluence/jira-url>/plugins/servlet/samlsso. | |
| IdP Certificate | Paste the BASE64-encoded Token Signing Certificate here. If you leave this field empty, the SAML response signature validation is disabled. This can be useful for testing and troubleshooting, but it's strongly recommend to enable the validation. Otherwise, attackers could gain access by sending fake SAML-responses. After clicking Send, the certificate is shown in the field below in readable form. |